Cyber-protection advice for hospital MEP systems

Cyber-risk increases as buildings and equipment become smarter, more connected and more reliant on networks.
Image by Getty Images
Vulnerabilities to health care mechanical, electrical and plumbing (MEP) cyberthreats include the disabling of a life safety system, equipment damage, disruption of facility operations or creation of a cyber entry point to a larger hospital network. Cyber-risk increases as buildings and equipment become smarter, more connected and more reliant on networks.
Cyber-risk mitigation is the least expensive and most effective when implemented at the initial planning stage of a project. A thoughtful cyber-risk process addresses the safety, efficiency and compliance goals of the health care facility. When executive leadership empowers information technology, operational technology and facilities professionals, an effective cyber-risk mitigation plan can be enacted.
This article, which is excerpted and adapted from the American Society for Health Care Engineering (ASHE) monograph “Best Practices Framework for Health Care Cyber Protection of MEP Systems,” presents a holistic design and construction process to set up owner operations for success. While it is directed toward new construction projects, the principles may be applicable elsewhere.
Protecting OT systems
In the past, a building’s MEP and support systems were less intelligent, separated or in figurative silos. Today, these systems are intelligent, programmable and network-capable out of the box. These advances in equipment technology offer a safer, more efficient and more compliant environment for people but also increase cyber-risk for the facility.
The existing cyber-protection culture mainly focuses on information technology (IT), but there is also significant cyber risk to operational technology (OT) systems, including electrical building systems, mechanical building systems, low-voltage building systems and architectural systems. For example, consider malware adversely affecting or disabling the medical gas, fire alarm or emergency generation systems.
Some key steps for developing a safer OT system are discussed here. The ASHE monograph describes these and other measures in significantly more detail.
Best practices framework. The best practices framework is the backbone of the ASHE monograph and an important first step that guides interactions between the design team and owner during project delivery and provides a long-term map for building cybersecurity, cyber sustainability and resilience, and deployment of new technology and software updates. The framework presents a series of steps to be followed from the initial project planning stage through the client takeover stage:
- Issue an executive directive for OT cyber protection. An executive directive identifies OT cyber protection as a measurable part of the project, which aligns priorities for the construction project team and provides resources for support. Key stakeholders are identified, and the roles and responsibilities of the team are established.
- Establish an OT project cyber project timeline. A project kickoff meeting initiates the integration of an OT cyber project process into the design and construction schedule, providing a realistic construction path to address cyber-risk concerns.
- Hold integration and technology visioning sessions and develop an associated OT cyber-risk management framework. These tasks set the project up for success by identifying the level and expectations of project integrations and associated cyber risks. The integration vision is developed, which identifies how the integration of systems will benefit patient care, staff workflow and processes as well as building efficiency measures that meet the safety and operational goals of the facility.
- Issue a project cyber plan. The project cyber plan provides a basis for the project, which can be communicated to the construction project team by the owner’s OT cyber subject matter expert (SME).
- Develop use cases. Developing project-specific use cases based on the visioning session starts the process to include specific desired outcomes (of the visioning session) in the project contract documents. Outcomes are realized through the commissioning of a use case or cases.
- Issue cyber-ready contract documents. Including cyber-ready specifications provides clear direction for the contractor and equipment manufacturers about how the project will be constructed per the project cyber plan.
- Integrate OT cyber efforts in the construction process. This includes validating the submittal requirements, data collection for the inventory of devices, network development and practices, and test bed development during project construction.
- Commission building operations and cyber elements and turn the system over to the owner. After use cases are demonstrated to the owner and it is verified that the OT network and devices are hardened per the contract documents, the owner takes over all cyber updates and maintenance items as well as continuous monitoring for fault/intruder detection and incident response.
Roles and responsibilities. Cyber protection of MEP systems is a new part of the construction process, and assigning roles and responsibilities within the project allows for a more streamlined approach to the design-bid-build process to develop the best practices framework for health care cyber protection of MEP systems. The following are the roles and responsibilities of team members on the cyber project team (a much more in-depth discussion of the roles of the owner, MEP engineer and the OT cyber design SME is included in the ASHE monograph):
Executive leadership and C-suite. An executive directive from the organization’s executive leadership will drive education, resources and, most importantly, buy-in from all team members, streamlining the process. IT cyber specialists agree that planning cyber solutions early provides better protection and is a much better use of resources.
- Owner project manager (PM). The owner PM’s responsibility is to drive the use case and cyber-protection project process and validate that all OT firmware and software patches are updated through the warranty period.
- Owner (OT) cyber SME. The owner OT cyber SME is responsible for project oversight, including ensuring that the project adheres to the owner’s policies and procedures and that it will achieve acceptable risk tolerance goals.
- Facility director. The facility director communicates operational and energy efficiency goals to the design engineer, ensures long-term operational success of the design per facility maintenance processes and works closely with the OT network maintenance personnel to validate that the process for patching and upgrading OT systems is in line with ongoing building operations.
- IT representative. The IT representative communicates the IT and security requirements to the project team, including the needs of business and clinical IT systems.
- Architectural PM. The architectural PM’s responsibility is to be aware of and drive the use case and cyber-protection project process.
- Design engineer. The design engineer integrates the contractor’s OT cyber design SME requirements into the contract documents and clearly communicates the use case scope in the contract documents — both critical steps for an accurate bid, construction and commissioning process.
- OT cyber design SME. The OT cyber design SME provides project cyber design leadership for the built environment to the design team and supports the owner’s OT cyber SME through the incorporation of the OT project cyber plan requirements into contract documents.
- Integration contractor. The integration contractor is possibly the most qualified to provide lessons learned based on their history of constructing OT networks. The contract documents, with input from the owner’s OT cyber SME, provide the integration contractor with the necessary direction to bid and build the project. This person is also the likely candidate to populate the construction schedule with milestones and submittal requirements and works closely with other contractor team members during the bid, shop-drawing and build phases of the project.
The integration contractor oversees use case progress and validates that use cases are realized. The OT internet protocol (IP) inventory of devices is consolidated and submitted by the contractor. Depending on the owner’s and general contractor’s preference for implementing modern building technology, the integration contractor may be the building management system controls contractor.
- General, electrical and mechanical contractors. The general, electrical and mechanical contractors validate that owner cyber elements are included in the bid and confirm cyber deliverables are included in the construction schedule. The owner’s OT cyber SME will have action items to be tracked in the construction schedule.
Each contractor needs to understand the requirements of the owner’s OT cybersecurity guidance document as it pertains to their scope. Confirming that use cases are correctly coordinated between specifications and contractors is a key element of success. The OT IP inventory of devices will be routed from the device manufacturer through the general, electrical and mechanical contractors to the integration contractor.
- Equipment manufacturers. Equipment manufacturers continue to innovate and introduce new products and solutions. Offering education (such as manufacturers’ educational sessions) on how these new solutions provide cyber-protective value to owners, in terms the design engineer and facility director can understand, encourages product advancement that may directly relate to a more resilient cyber-protective system.
Cyber project timeline. Integrating an OT cyber project process into the design and construction schedule provides a realistic path to address cyber-risk concerns. A RACI chart clarifies roles and responsibilities for each task: the person (R)esponsible does the work for the person (A)ccountable for the task, or the decision-maker. The (R)esponsible person will either get direction from persons they (C)onsult or be given authority to complete the work and only (I)nform certain persons. The project timeline includes the following task and deliverable stages:
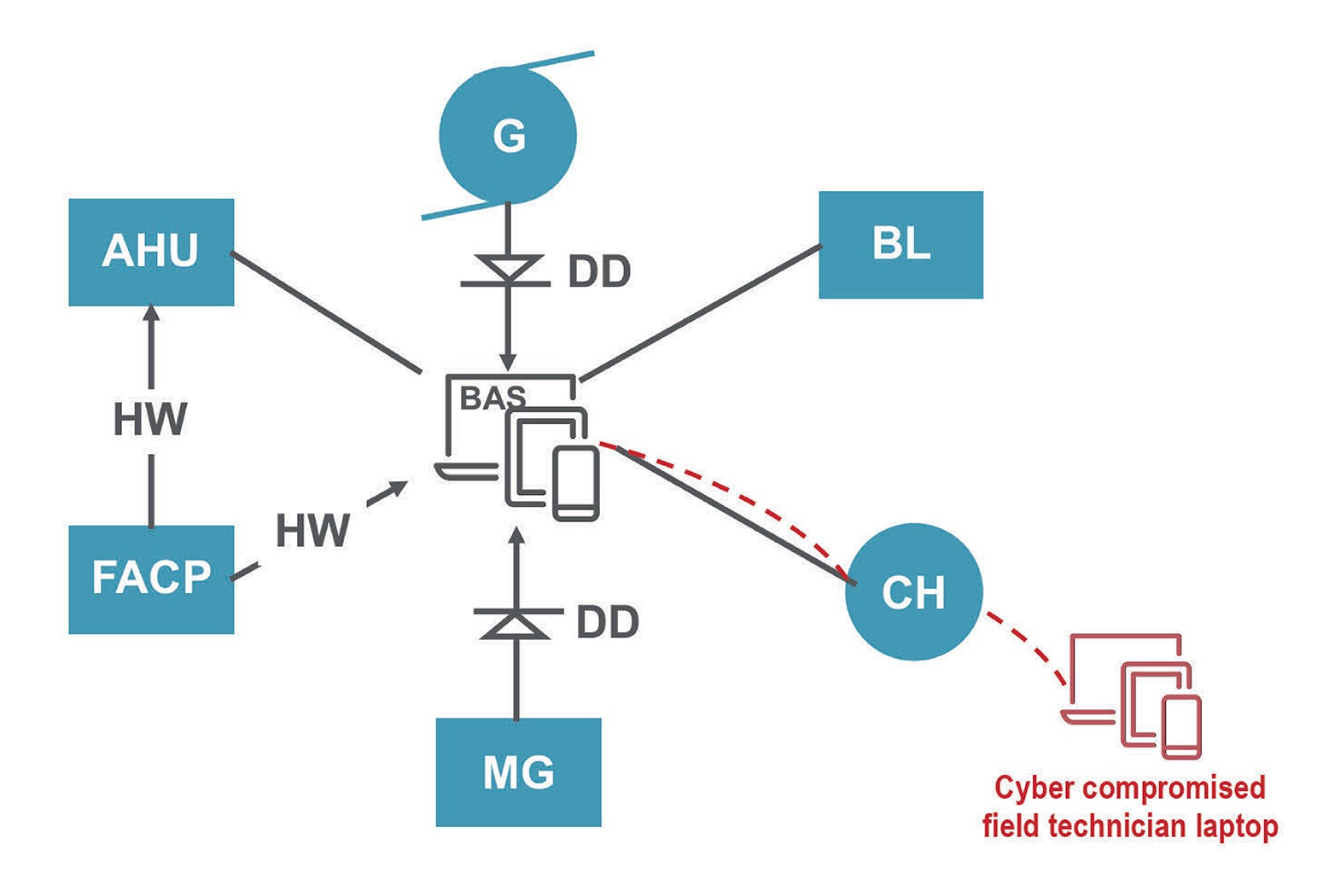
An example of a cyber-compromised operational technology network in a cyber-protected integrated building. Click image to enlarge
- Planning. During the planning stage, the project executive leadership identifies OT cyber protection as a measurable part of the project. The integration vision is developed, which identifies how the integration of systems will benefit patient care, staff workflow and processes as well as building efficiency measures that meet the safety and operational goals of the facility. Integration outcomes provide the roadmap to develop use cases in the next phase.
- Schematic design. During the schematic design phase, each OT system is identified. Use cases are developed such that implementing a group of discrete use cases will accomplish each integration outcome. Each use case is a real, achievable exchange of data between two or more systems that can be commissioned. Also during this phase, the OT cybersecurity guidance document is addressed for the specific project.
- Design development. Finalizing the use cases and updating project specifications to support the construction and commissioning of each use case is the next step. The scope is also defined for the execution of each use case. For example, if the owner purchases the nurse-call system, the owner is responsible for the electronic health records for nurse-call data integration.
- Contract documents. The owner’s health care cyber requirements for OT or the OT project cyber plan is referenced or included in the contract document set.
- Construction schedule. The general contractor is directly or indirectly responsible for the integrations and includes the deliverables from both the contractors and owner in the construction schedule.
- Shop drawing. During the shop-drawing process, the integrating contractor provides the number of IP addresses required for the OT network and submits a proposed OT network design based on the owner’s OT cybersecurity guidance document. Per the construction schedule, the owner will provide the IP addresses and approval of the OT network.
The owner also coordinates the delivery date of any owner-provided devices (e.g., firewall and switches). Typically, a large number of team members have access to view submitted shop drawings, so consideration should be taken when submitting the master username and password list to limit viewers.
- Substantial completion. After equipment is delivered to the site, the integration contractor develops an OT IP inventory of devices. After the building telecommunications rooms are ready to accept IT/OT equipment, the OT firewall and switches will be configured and installed based on the preliminary IP inventory of devices. The contractor may transfer network connections from the construction staging switches to the permanent OT switches and verify that all cyber configurations support building operations. After a successful transition to the permanent switches, the OT IP inventory of devices may be transferred to the owner. If a test and development environment is part of the project, it should be completed at this project phase.
- Commissioning. Commissioning has multiple parts, including demonstrating to the owner that each device is configured per the owner’s OT cybersecurity guidance document; demonstrating that each use case will function correctly; auditing network configuration, including firewall rules and segmentation; and demonstrating test and development environment (if part of the project scope).
- Turnover. After the owner verifies that the OT network is installed per the OT cybersecurity guidance document, the owner takes over all cyber updates and maintenance items as well as continuous monitoring for fault/intruder detection and incident response.
New type of risk
The concept of risk management is not new to design and construction projects. Health care facilities professionals design to standards and codes that were adopted to lower other types of risks such as fire, flood and wind. Now is the time to transition planning to include cybersecurity as a risk that should be addressed like any other.
Cybersecurity risks will continue to evolve and advance, as will the societal need for integration of smart devices to achieve goals for efficiency, sustainability, convenience and overall patient outcomes. This framework represents a deliberate, collaborative and scalable approach that will achieve the owner’s risk management goals and is fully supported by the comprehensive project team.
Solutions implemented during construction typically have minimal cost impacts on the overall construction budgets and allow for systems to be commissioned with cybersecurity integrated rather than being bolted on during facility operations, which makes them more difficult to implement and therefore more costly, due to coordination with an operating facility.
About the ASHE monograph
The American Society for Health Care Engineering’s (ASHE’s) new monograph, “Best Practices Framework for Health Care Cyber Protection of MEP Systems,” is the result of a collaborative effort from projects where information technology and integration contractors partnered with a construction project team to contribute operational technology cyber solutions and methods in project contract documents, including contributors to the 2020 ASHE monograph “Best Practices Framework for Health Care Cyber-Physical Protection for the Construction Project Team,” which the new monograph updates.
Authors
ASHE thanks the authors of the new monograph:
- Tim Koch, PE, SASHE, LEED AP, is a vice president and engineering principal at HDR in Omaha, Neb.
- David Brearley, GICSP, PMP, CISM, is a senior professional associate and the operational technology cybersecurity director at HDR in Charlotte, N.C.
- Kent Choma, PE, Ph.D., is the market director of plant operations for the Northern Nevada Health System.
- Owen Redwood, CISSP, GICSP, Ph.D., is an advisor to the Biohacking Village and a principal security researcher at Research Innovations Inc.
- Janine (Nina Alli) Medina, MS, is co-founder of the Biohacking Village and its executive director for the past seven years.
Contributing author
Additionally, ASHE thanks the monograph’s contributing author:
- Chuck Sloup is a senior commissioning engineer at HDR, where he serves a variety of government and private clients.
This article was excerpted and adapted by Health Facilities Management staff.




